Developers store their code for projects in a repository tool called Version Control System (VCS). It records every code change, who made the change, and when the changes were made. Housing all the information in one place makes it much easier for developers to manage all code changes.
A VCS can help your web development team dramatically. One of the most popular options is Git, an open-source distributed variant of VCS. The “distributed” features of GIT enables all users to have a copy of the repository data stored on their computer. It allows users to store code change databases in their local repository, and no central server is required to collect each code change. The developers don’t need a network or the Internet to store their work when they have finished.
There are a few reasons why this is beneficial:
- Users can work offline because all data is local.
- It doesn’t depend on a centralized server, so if the server goes down, you will not lose the only copy of the project files.
- It processes data quickly because it doesn’t have to communicate with a central server constantly.
- It pushes a copy of your files to a web server. That way, when an accident occurs on your computer, you have a complete copy of the file located on your web server, which makes it possible to configure the server repository to push new changes to your website.
A distributed VCS enables developers to work from anywhere. Instead of using the Internet to store their work, they only need to keep their code in a local repository and push it into the cloud once they have Internet access. However, this feature can cause difficulties if the developers don’t carefully manage the cloud architecture with security in mind.
Information Disclosure Risk
Information disclosure, also known as information leakage, is when a website unintentionally reveals sensitive information to its users, such as:
- Customers or users’ private information such as name, address, and financial data
- Valuable sales and business information
- Information about website technical details or website infrastructure
When this happens, the consequences can be devastating for the organization and developers alike. Often, the attacker’s entry point when orchestrating an attack is from infrastructure vulnerability such as Git, where they will scour for information disclosure and use that information to penetrate and gain access to the web application. Hence, one way to prevent security breaches to your web application is to inspect your Git setup for possible information disclosure and remove any vulnerability found.
How To Test Git Information Disclosure in a Website
An easy way to test whether a site git folder is exposed to the network is by typing ‘.git’ after the domain or sub in the site, for example, http://example.com/.git. If the display result is in a folder list/folder index, it means that the current site has a security issue via Git.
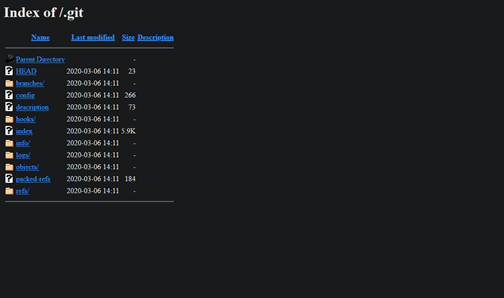
At this stage, an attacker will easily collect all the site sources and all history changes based on the git source.
To get all sources, follow these steps:
- Go to the objects/pack folder.
- When you see the pack list file, download it all manually or use a third-party tool, such as download manager, to store all files in your local .git/objects/pack. Ensure to run Git in it first to create the .git folder.
- To extract the pack files, run git fsck –lost-found command in OS terminal/command prompt. You will shortly receive the commit history result stored in the current repository via git fsck.
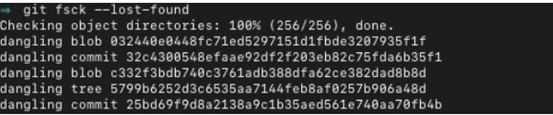
You can get all source files from any commit history from that source; for example, we run git checkout to commit code 32c43xxxxx.

Now, all source code is based on that commit. Just browse via file manager or IDE tool to get the detailed info from each code file. Suppose the developer accidentally stores some credentials in the repository. In that case, it will take a long time to end this security issue report because it will most likely produce another security issue based on finding via Git.
Tool to Test
Usually, DevOps have already set the directory if it does not have an index file. But sometimes, they forget that the attacker can still access the file directly. You can access some default files generated from Git to access the detailed file during the first time of the test. The attacker can still download the source based on information they received earlier.
Testing the information disclosure can be faster using a published tool on GitHub such as Git-dumper – one of the most used tools. Since this tool builds on top of Python, installing Python in advance is required. For detailed information and step-by-step instructions on using this tool, please visit this GitHub link: https://github.com/arthaud/git-dumper.
Conclusion
Putting the .git folder in a public directory should be avoided. Should the .git folder be stored on the public directory, ensure that all files in it are inaccessible from a browser or any tool from the public network. Otherwise, the .git folder, along with the directory list, will be accessible and collectable easily using a crawling robot such as Google search engine. Moreover, depending on the cache, certain search engines can keep it for the next few times.











