It is vital to be highly aware of the cyber security threat processes to keep your system safe in today’s world, where information security is crucial.
One process that plays a crucial role in cyber security threats is reconnaissance. In the context of cyber security, reconnaissance is a process that mainly focuses on collecting as much information as possible related to the target. Reconnaissance is a step that helps a hacker determine whether a system will be complicated or easy to penetrate. Reconnaissance can come in two forms: passive and active.
Passive Reconnaissance
Passive reconnaissance collects information related to the target without directly accessing the target endpoint or network. This part is relatively hard to detect because the system does not recognize the hackers. Hackers can obtain information from the target IP addresses and personal information such as names, emails, phone numbers, addresses, domain data, subdomains, related URLs, etc.
Here are a few well-known examples of passive reconnaissance tools.
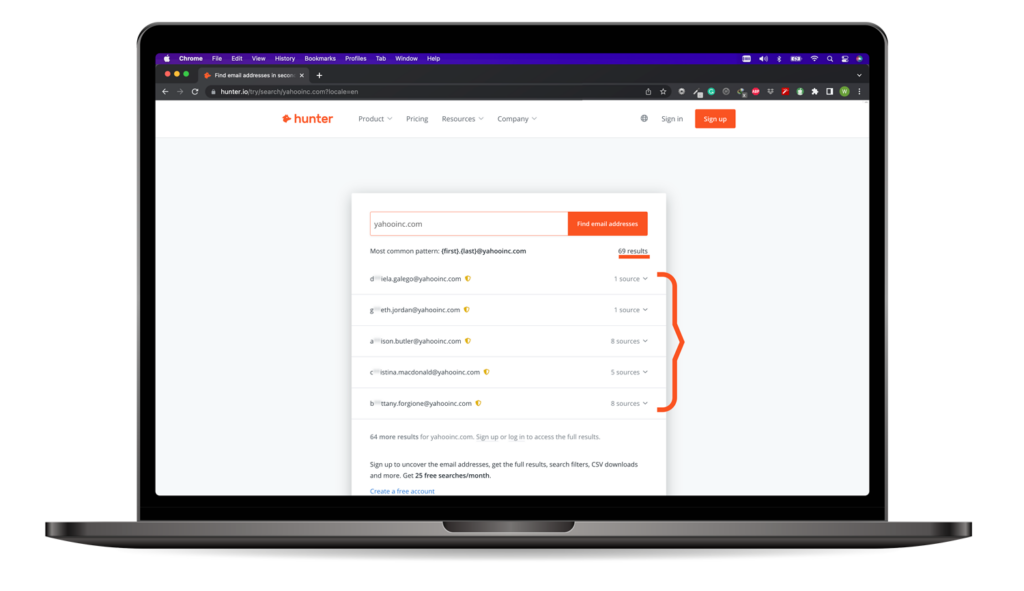
Whois
Mainly for collecting information related to the target domain. You can obtain the name and server link information with Whois, the domain registrant’s email and phone number, important dates related to the domain, and much more.
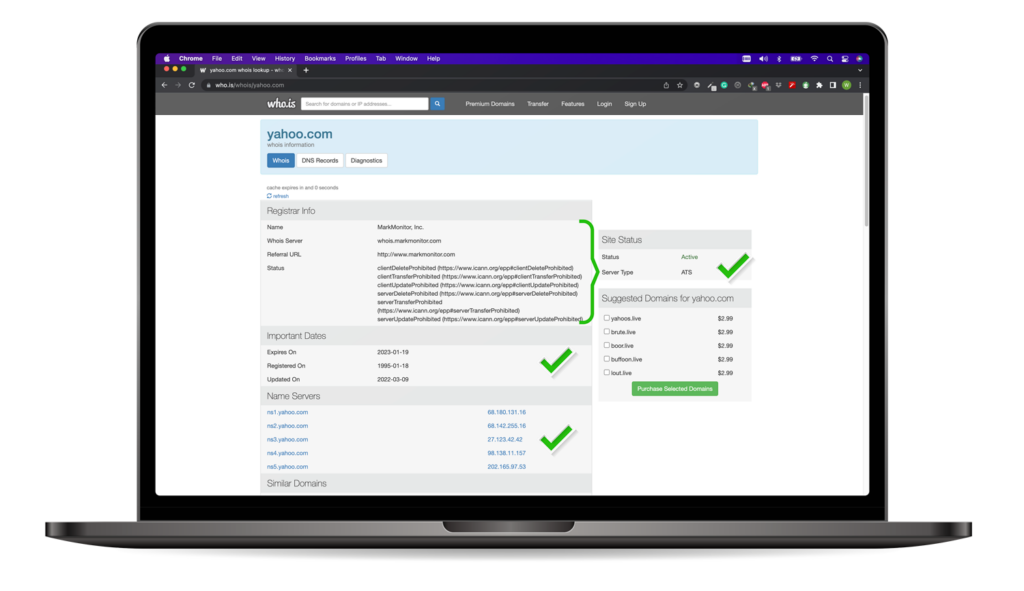
Shodan.io
Shodan.io is a search engine like Google, but unlike Google, Shodan is used to collect information on devices connected to the internet. By using Shodan.io, we can find subdomains related to the target.
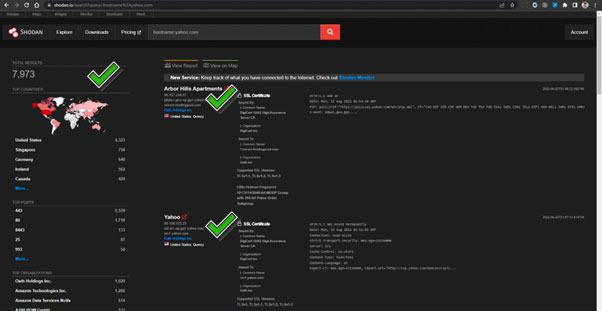
Hunter.io
Hunter.io is commonly used to find email addresses related to the target in seconds.
Active Reconnaissance
Active reconnaissance is a process of gathering information by trying to access the target endpoint or network. This process has the advantage of providing more relevant data than passive reconnaissance but has the drawback of alerting the system to the presence of an attacker. When the system detects the hacker, typically, it will ban the hacker’s IP Address so they cannot access the target anymore. There is essential information that hackers can gather from this process, for example, relevant subdomain, hidden directories, open ports, and many more.
Here are a few examples of active reconnaissance tools.
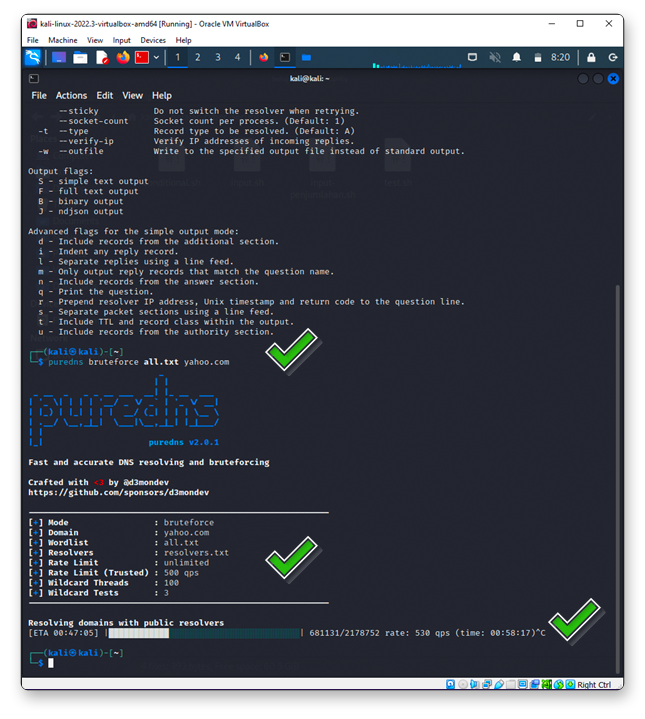
Puredns
Just like Shodan.io, Puredns is used to look for any subdomains related to the target domain.
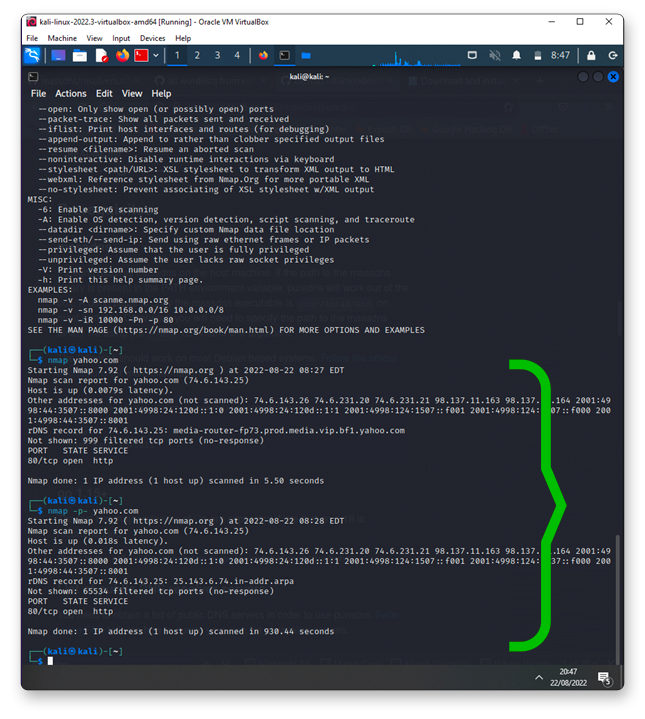
Nmap
Nmap has several features, but it is mainly used to scan a system network to reveal its weaknesses, such as open ports and other potential entry points.
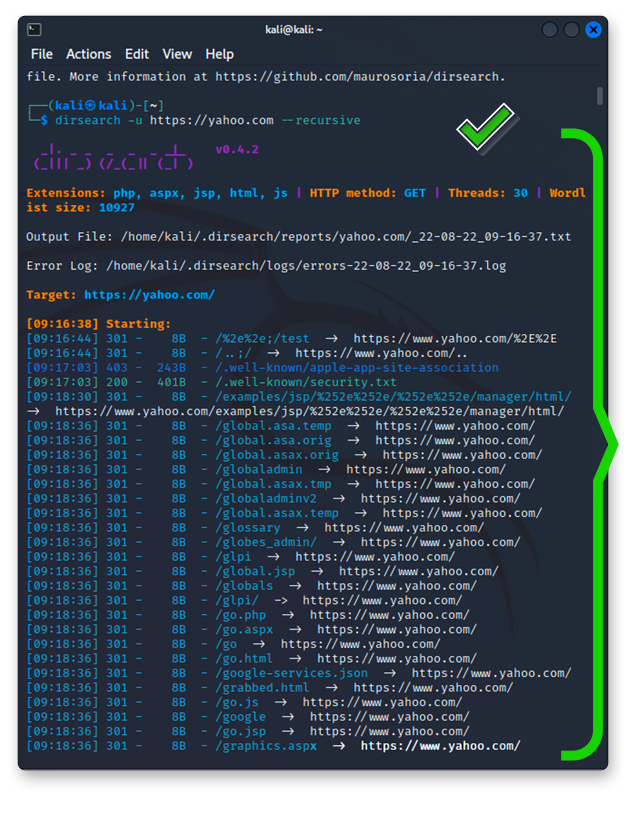
Dirsearch
Dirsearch is used to scan a directory and files contained in the target.
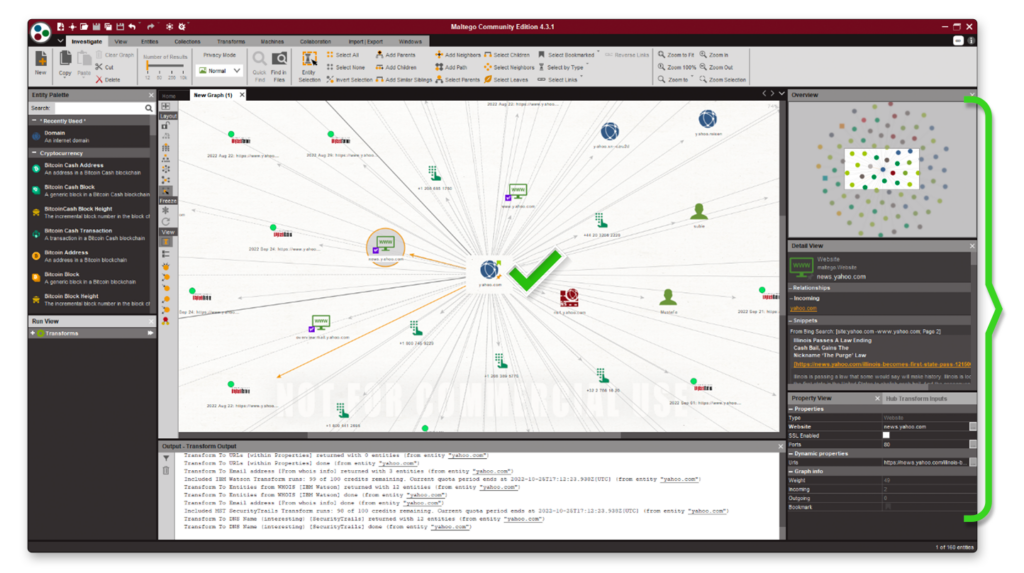
Maltego
Pre-installed in Kali Linux, Maltego is a one-stop tool to gather information about people, companies, organizations, websites, domains, DNS names, IP addresses, and many more. The data that Maltego gathers can be depicted in a graph format, a visually rich and powerful reconnaissance tool.
Conclusion
Reconnaissance is an essential step in cyber security. Any information collected in this process could be used to exploit vulnerabilities on its target. While it is impossible to create a perfectly secure system, we can mitigate against attack risks by understanding the process and building countermeasures to prevent them, thereby providing increased security on our system.
Author: Indra Budiman, Software Engineer, Programmer











