In today’s fast-paced digital world, the need for secure software is more pressing than ever. DevSecOps, a transformative approach to software development, integrates security practices into the DevOps model. This fusion ensures that security is not an afterthought, but a continuous process ingrained in every phase of the development lifecycle. Let’s delve into the key components of DevSecOps and explore how it facilitates the process of building secure software without compromising speed and agility.
Understanding DevSecOps
The Evolution of DevSecOps
Traditional software delivery models treated security as a final gate — often a manual penetration test before release. In the DevOps era, that bottleneck became a liability. DevSecOps evolved to embed security early (“shift left”) and throughout the lifecycle.
- DevOps = speed and automation.
- Security = governance, compliance, and risk management.
- DevSecOps = automation + collaboration + continuous security.
By integrating security checks directly into CI/CD pipelines, teams eliminate silos, detect vulnerabilities earlier, and reduce both risk and remediation costs.
Key Principles of DevSecOps
The core principles of DevSecOps revolve around three main concepts: collaboration, automation, and continuous improvement.
- Collaboration – Security becomes a shared responsibility across developers, operations, and security engineers. GitOps and ChatOps workflows foster transparency and ownership.
- Automation – Security tasks (testing, scanning, compliance checks) are automated in CI/CD pipelines to avoid slowing down deployments.
- Continuous Improvement – Security posture is continuously refined with threat modelling, red-teaming, and lessons learned from incidents.
These principles align with agile and cloud-native practices, ensuring that security scales alongside modern software delivery
Integrating Security into DevOps
Integrating security into the DevOps workflow requires a shift in mindset. It involves embedding security practices into every stage of the development lifecycle, from design and coding to deployment and maintenance. This approach ensures that potential security issues are identified and resolved early on. A modern pipeline may include:
- SAST (Static Application Security Testing): SonarQube, Semgrep.
- SCA (Software Composition Analysis): Snyk, OWASP Dependency-Check, WhiteSource.
- DAST (Dynamic Application Security Testing): OWASP ZAP, Burp Suite.
- Container & IaC scanning: Trivy, Checkov, tfsec, kube-bench.
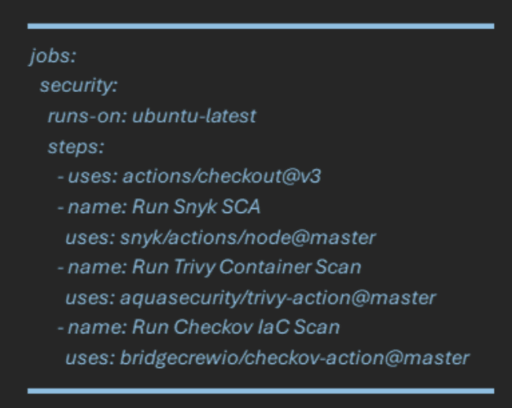
Example GitHub Actions snippet:
This ensures every code change is scanned before merging — enforcing security as code.
Secure Coding Practices
Why It Matters
Secure coding is a fundamental aspect of DevSecOps, aimed at preventing vulnerabilities during the software development phase. By adhering to secure coding practices, developers can prevent common security issues like SQL injection, cross-site scripting, and buffer overflows.
The importance of secure coding cannot be overstated. It ensures that software behaves as intended and prevents unauthorized actions that could lead to data breaches or other security incidents. Secure coding is not just about writing code; it’s about writing code that is secure by design.
Adopting secure coding practices requires a comprehensive understanding of potential security threats and how they can be mitigated. This is often facilitated through training and awareness programs for developers to ensure they are well-versed in the latest security vulnerabilities and how to address them.
Techniques for Secure Coding
- Input validation: sanitize user inputs to prevent injection attacks.
- Authentication & authorization: use strong libraries (e.g., JWT, OAuth2) instead of rolling your own.
- Code reviews with security focus: pair programming, PR reviews, and tools like SonarQube.
- Secure dependencies: pin versions, run SCA scans, update regularly.
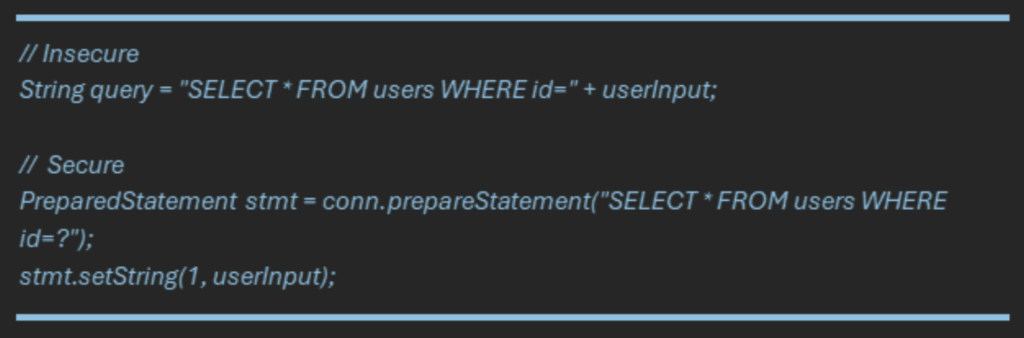
For example, never concatenate SQL strings directly:
Challenges and Solutions
While secure coding is essential, it presents certain challenges. One of the primary challenges is the balance between performing exhaustive security checks and maintaining development speed. This is where automation and tooling play a crucial role.
Integrating automated security tools within the development pipeline can help in identifying vulnerabilities without slowing down development. Tools like OWASP ZAP and SonarQube offer powerful capabilities to detect and manage vulnerabilities effectively.
Educating developers about secure coding practices is equally important. Regular training sessions and workshops ensure that developers stay current with the latest security trends and practices, fostering a proactive security culture within the organization.
Automated Security Testing
Why Automate?
Manual reviews don’t scale in cloud-native environments. Automated security testing provides continuous, scalable, and repeatable assurance.
Types of Automated Security Tests
- SAST: scans code at rest for vulnerabilities.
- SCA: analyses dependencies for known CVEs.
- DAST: simulates real attacks on running apps.
- IAST (Interactive Application Security Testing): combines static and dynamic testing inside running apps.
- Fuzz testing sends random inputs to detect crashes or unexpected behaviours.
Tooling Examples
- Semgrep for code scanning.
- Trivy for container/image scanning.
- OWASP ZAP for DAST.
- Burp Suite Pro for advanced security testing.
The goal is to run these tests in parallel with builds — providing developers immediate feedback without slowing release velocity
Infrastructure as Code
Introduction to Infrastructure as Code (IaC)
Infrastructure as Code (IaC) is a pivotal concept in DevSecOps, enabling the management and provisioning of infrastructure through code. It treats infrastructure as software, using configuration files that enable version control and automation.
IaC plays a significant role in ensuring security by enabling consistent infrastructure setups across different environments. This consistency helps mitigate configuration drift, a common source of security vulnerabilities, ensuring that every instance is compliant with security policies.
The use of IaC allows for quick and efficient infrastructure deployments, facilitating agile practices within development teams. It supports scaling and adapting infrastructure dynamically, aligning with the rapid pace of modern software development.
Secure IaC Practices
Cloud-native teams manage infrastructure with Terraform, AWS CloudFormation, or Kubernetes manifests. While this accelerates provisioning, misconfigurations can be catastrophic.
Best Practices
- Version control all IaC (GitOps).
- Scan IaC using tools like Checkov, tfsec, Terrascan.
- Secure secrets: never hardcode credentials; use Vault, AWS Secrets Manager, or Kubernetes Secrets with encryption.
- Policy as Code: enforce compliance with OPA (Open Policy Agent) or Conftest.
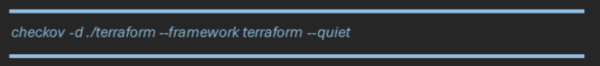
Example Checkov scan in CI/CD:
This detects misconfigured S3 buckets, open security groups, or missing encryption at deploy time.
Continuous Monitoring and OWASP
The Importance of Continuous Monitoring
Continuous monitoring is an essential component of DevSecOps, providing real-time insights into the security posture of applications and infrastructure. It involves constant observation and analysis of systems to detect potential security threats and ensure compliance.
The importance of continuous monitoring lies in its ability to offer proactive threat detection and rapid incident response. By continuously assessing the security state, organizations can identify vulnerabilities and address them before they escalate into critical incidents.
Continuous monitoring also supports compliance efforts, as it provides the necessary data to demonstrate adherence to security policies and regulatory requirements. This capability is invaluable in maintaining customer trust and avoiding legal penalties.
Implementing Continuous Monitoring Tools
Implementing continuous monitoring requires a combination of tools and processes tailored to the organization’s needs. Tools like Datadog, Splunk, and Prometheus offer powerful monitoring capabilities, providing visibility into system performance and security events.
Shifting left is essential, but shifting right (runtime protection) is also equally important. Once deployed, apps and infrastructure must be monitored for anomalies.
Tools for Continuous Monitoring
- APM & Observability: Datadog, Prometheus, Grafana.
- SIEM/SOAR: Splunk, Elastic Security.
- Runtime security: Falco (Kubernetes), eBPF-based monitoring.
- Cloud security posture management (CSPM): Prisma Cloud, AWS Security Hub.
OWASP: A Key Resource
The Open Web Application Security Project (OWASP) is a key resource for organizations looking to enhance their security practices. It provides a wealth of information, tools, and guidelines designed to help secure software applications, making it an invaluable asset in the DevSecOps toolkit.
OWASP provides:
- OWASP Top 10 – critical web app risks.
- OWASP ASVS (Application Security Verification Standard) – detailed control checklist.
- OWASP SAMM – maturity model for secure development.
These resources ensure teams continuously align with global best practices.
Future of DevSecOps
Trends Shaping DevSecOps
The future of DevSecOps is shaped by several emerging trends. The rise of artificial intelligence and machine learning in security operations is transforming the way organizations detect and respond to threats, offering predictive capabilities and enhanced decision-making.
Looking ahead, several trends are shaping DevSecOps:
- AI-powered security: machine learning for anomaly detection, predictive vulnerability scanning.
- Policy-as-Code & Compliance-as-Code: codifying standards like CIS Benchmarks and PCI-DSS into CI/CD.
- Zero Trust architectures: enforcing least privilege across infrastructure.
- Shift everywhere: left (development), right (runtime), and deep (supply chain).
Security is no longer just about tools — it’s about building a culture where developers, ops, and security teams collaborate seamlessly.
Ethical Considerations
As DevSecOps practices evolve, ethical considerations become increasingly important. Ensuring data privacy and minimizing bias in security algorithms are critical issues that require careful attention. Organizations must prioritize transparency and accountability in their security initiatives.
Ethical considerations also encompass the responsible use of automation and AI in security operations. Ensuring that these technologies are used to enhance human judgment and decision-making, rather than replace it, is essential in maintaining ethical standards and trust.
Engaging with stakeholders, including customers and regulatory bodies, about security practices is crucial. Open communication and transparency help build trust and ensure alignment with societal expectations and legal requirements.
Conclusion
DevSecOps is not a tool you buy; it’s a culture and practice you build. By embedding automated security checks into CI/CD pipelines, coding with security in mind, securing IaC, and continuously monitoring runtime environments, organizations can deliver software that is both fast and secure.
The companies that succeed with DevSecOps won’t just avoid breaches, they’ll win trust, accelerate innovation, and future-proof their software delivery